Enhancing Linux Server Security: Advanced Practices
Written on
Chapter 1: Introduction
Linux is the preferred platform for many developers due to its speed, efficiency, and resource management. However, its default configurations may not align with your organization's security protocols. It is crucial to adhere to robust security measures and keep your systems updated with the latest protective features.
This article is the third installment in our series on securing Linux servers, following the previous two parts, which can be found here and here. In this section, we will delve into further security practices that are essential for both independent developers and administrators.
This video discusses how to secure your Linux server and create a Virtual Private Server (VPS) using Linode, providing essential steps and insights.
Chapter 2: Managing User Accounts
Section 2.1: Disabling User Accounts
Organizations often have specific protocols regarding user accounts when employees are temporarily absent or permanently laid off. A common approach is to disable the user account until further notice.
This measure serves two main purposes: it protects the system by preventing unauthorized access and reduces the risk of a compromised account. To disable an account, you can use the usermod or passwd commands. For instance, to deactivate Jack's account, execute:
usermod -L jack
or
passwd -l jack
The /etc/passwd file keeps track of registered accounts. Disabling an account adds an exclamation mark (!) in the second field of this file. However, if the user has created an SSH key, the account may still be accessible. In such cases, the chage -E0 command should be used:
chage -E0 jack
This command modifies the /etc/shadow file, effectively locking the account by setting the expiration date to January 1, 1970.
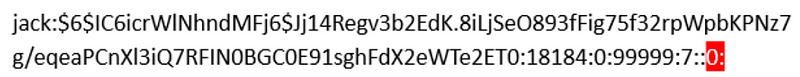
Section 2.2: Deleting User Accounts
When an account is no longer needed, it should be deleted to prevent any malicious activities. Use the userdel command to remove the user. For example, to delete Jack's account, run:
userdel jack
To also remove Jack's home and mail files, include the -r flag:
userdel -r jack
If Jack has any processes running, they should be terminated to avoid future inconsistencies. The killall command can be employed for this:
sudo killall -u jack
Alternatively, to forcefully remove the account even if the user is logged in, use:
userdel -f jack
Chapter 3: Implementing Restricted Shells
Section 3.1: Understanding Restricted Shells
A restricted shell limits the commands available to users, preventing potentially harmful actions. This is particularly useful in environments such as libraries or internet cafes. In Linux, you can use rbash (restricted bash) as the default shell.
To create a user with restricted access, use the following command:
sudo useradd jack -s /bin/rbash
Set a password for Jack:
sudo passwd jack
Create directories for Jack's files:
sudo mkdir -p /home/jack/bin
Modify the $PATH variable to restrict command access:
export PATH=$HOME/bin
You can add specific commands that Jack is allowed to use by placing them in the /home/jack/bin directory or creating symbolic links.
Section 3.2: Imposing Restrictions on Existing Users
To apply restrictions to an existing user, use the usermod command:
sudo usermod -s /bin/rbash tom
Chapter 4: Disabling USB Access
Depending on the criticality of the system, disabling USB ports may be necessary as they can be entry points for malware. To block USB access, modify the blacklist.conf file:
sudo nano /etc/modprobe.d/blacklist.conf
Add the following line:
blacklist usb_storage
Then, open the rc.local file:
sudo nano /etc/rc.local
Add these commands:
modprobe -r usb_storage
exit 0
Conclusion
This article shifted focus from individual development and web hosting to enterprise-level security for Linux systems. Implementing these advanced practices can significantly enhance the security of your Linux servers.
The second video highlights three essential Linux security settings that are crucial for every VPS. It covers foundational steps that everyone should implement for better security.